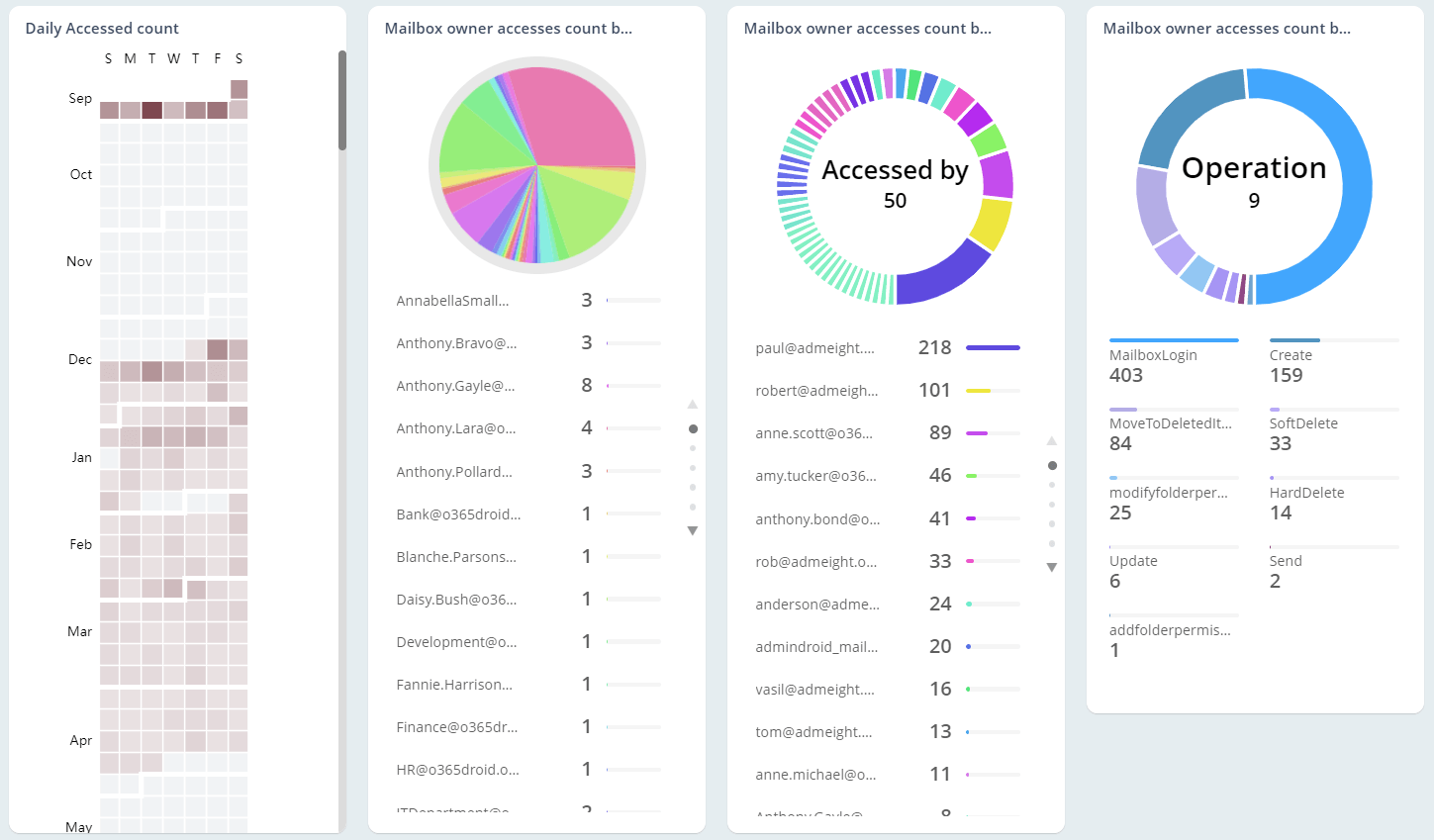
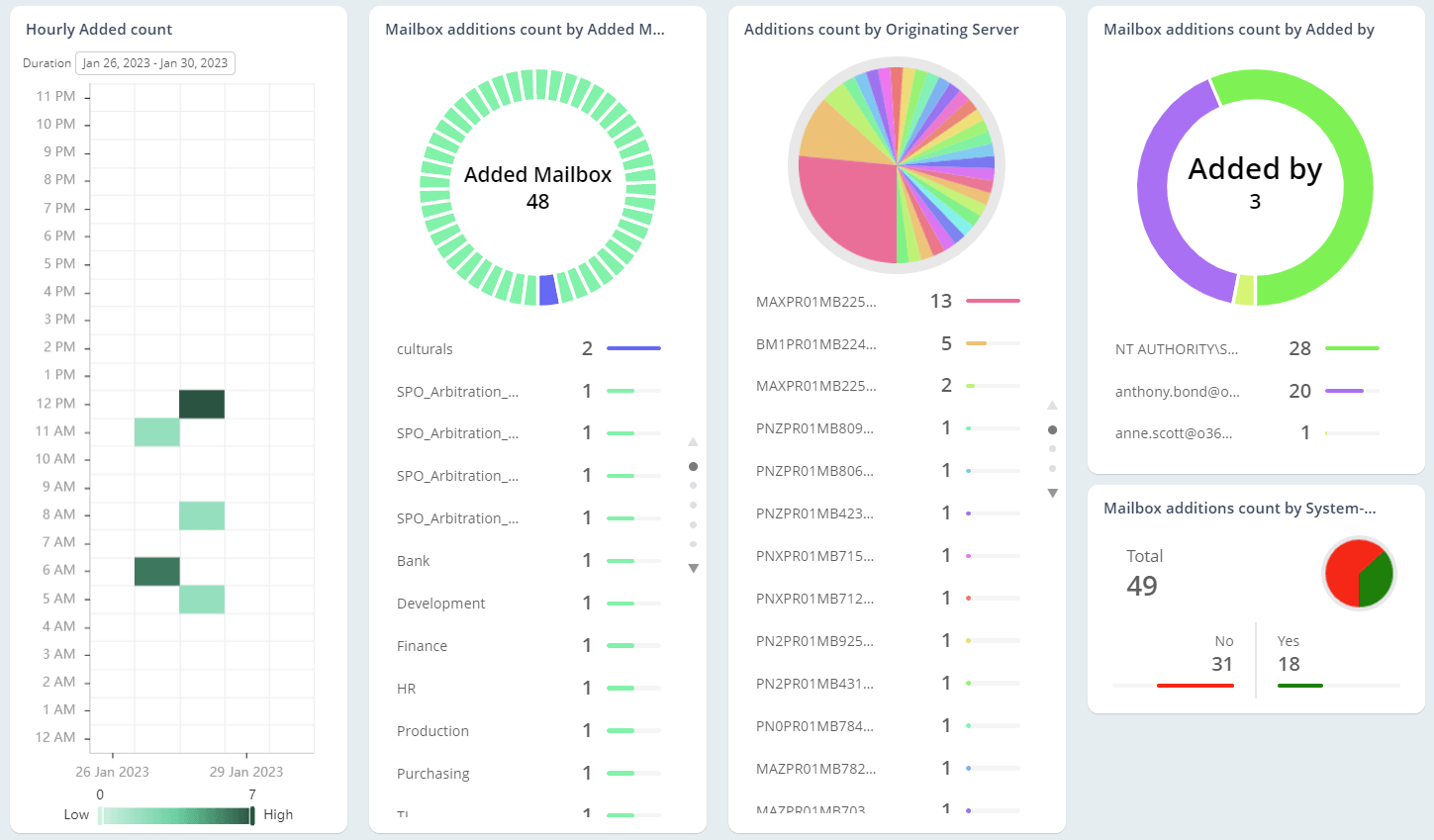
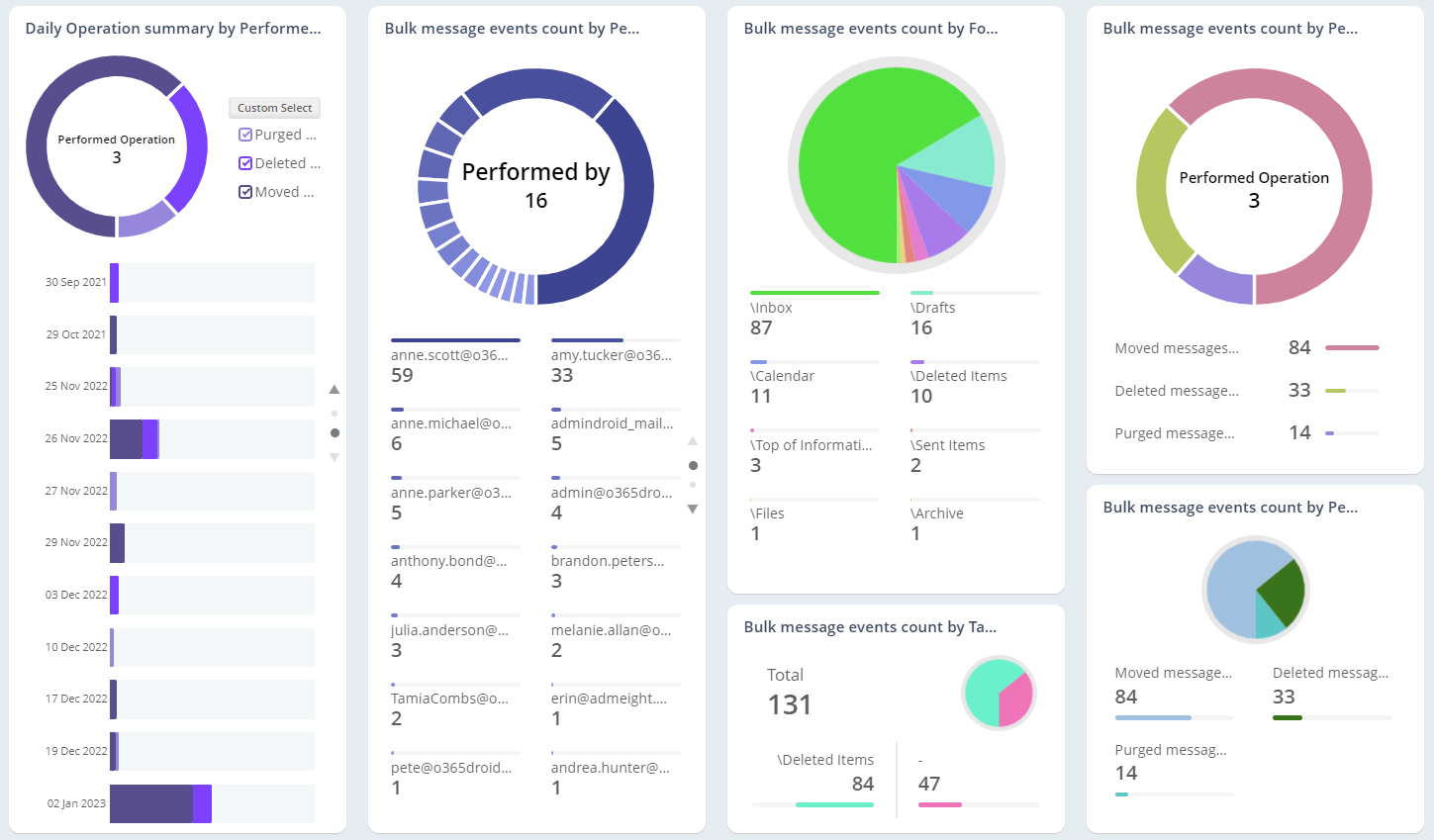
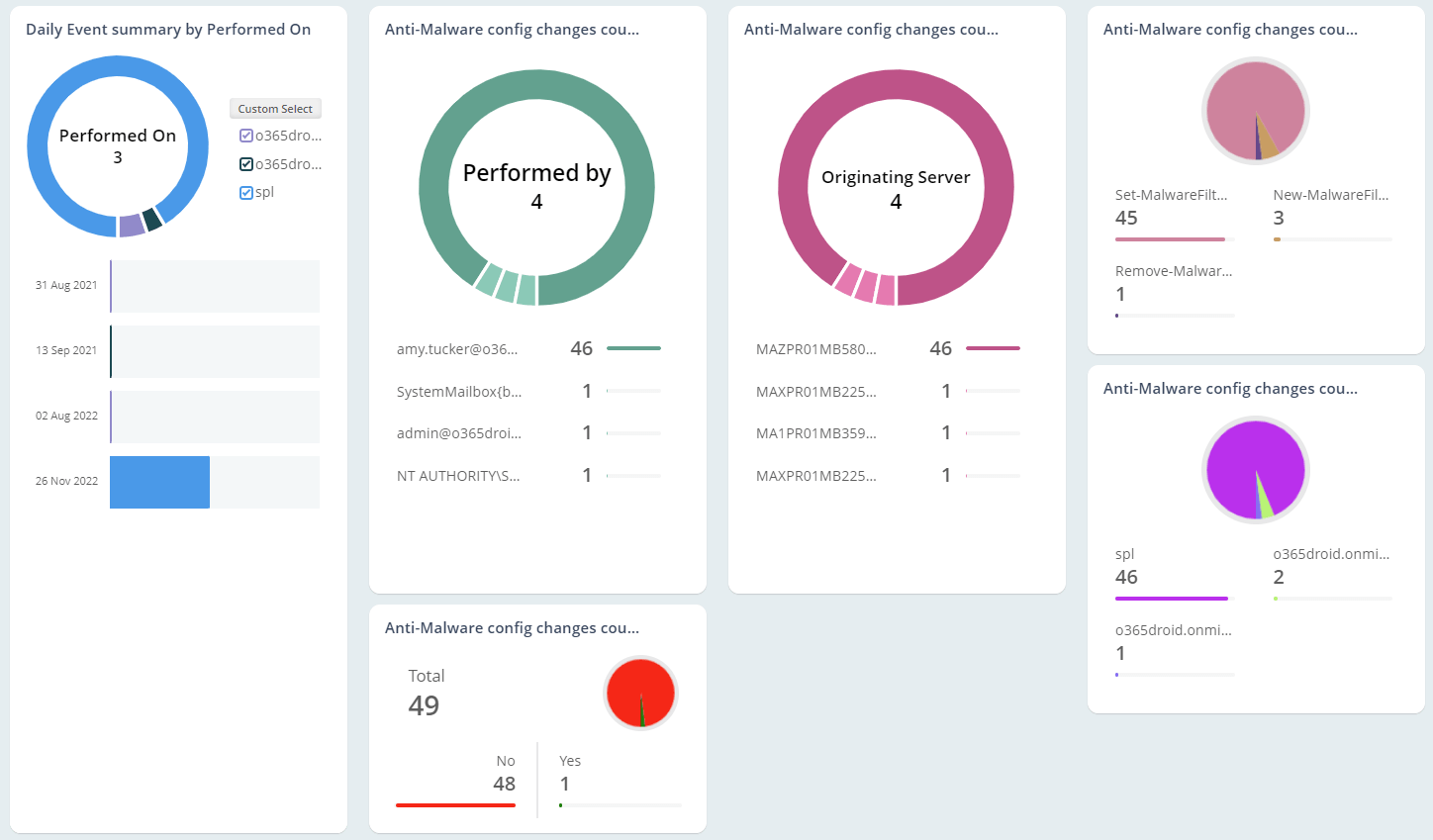
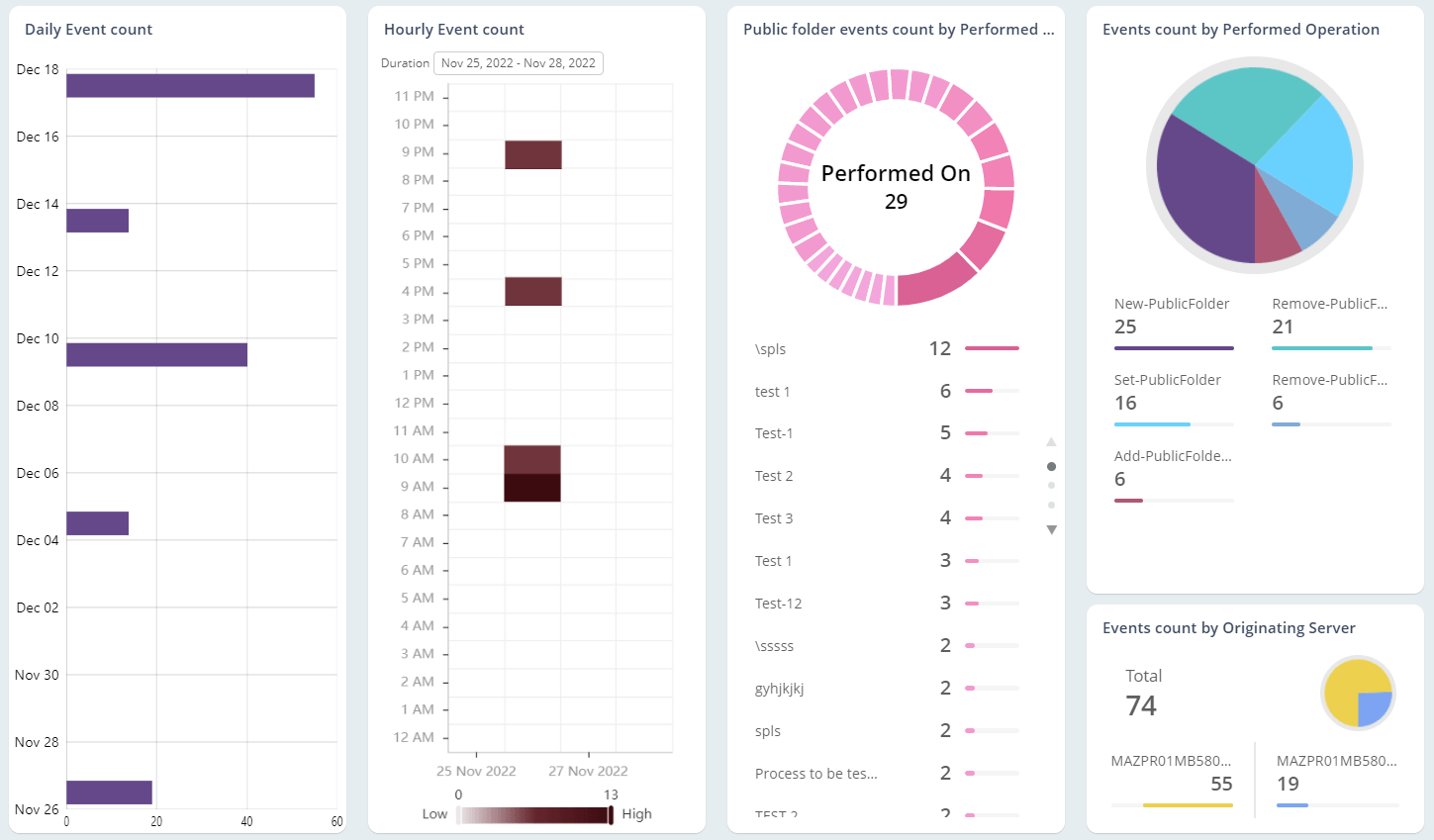
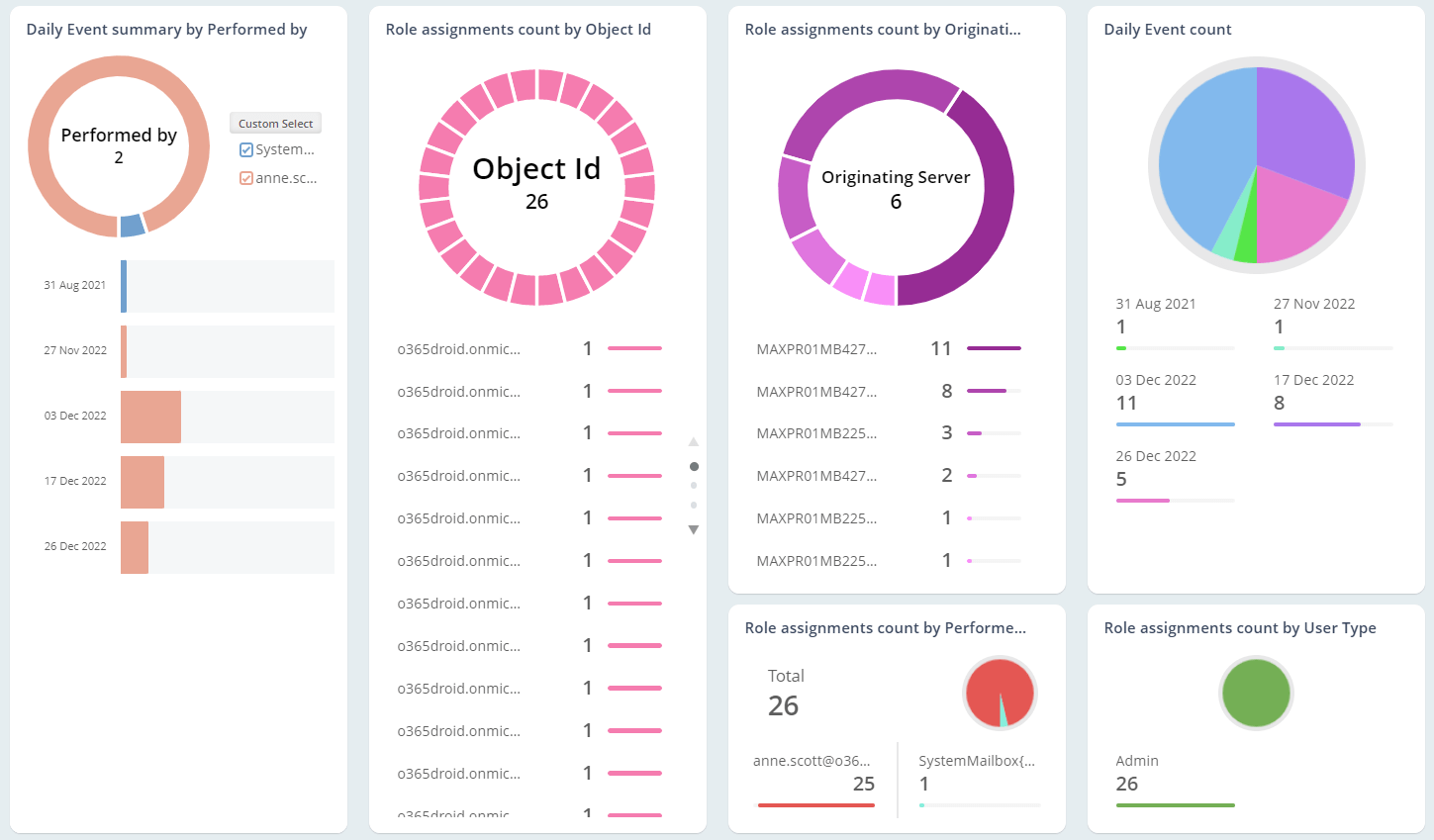
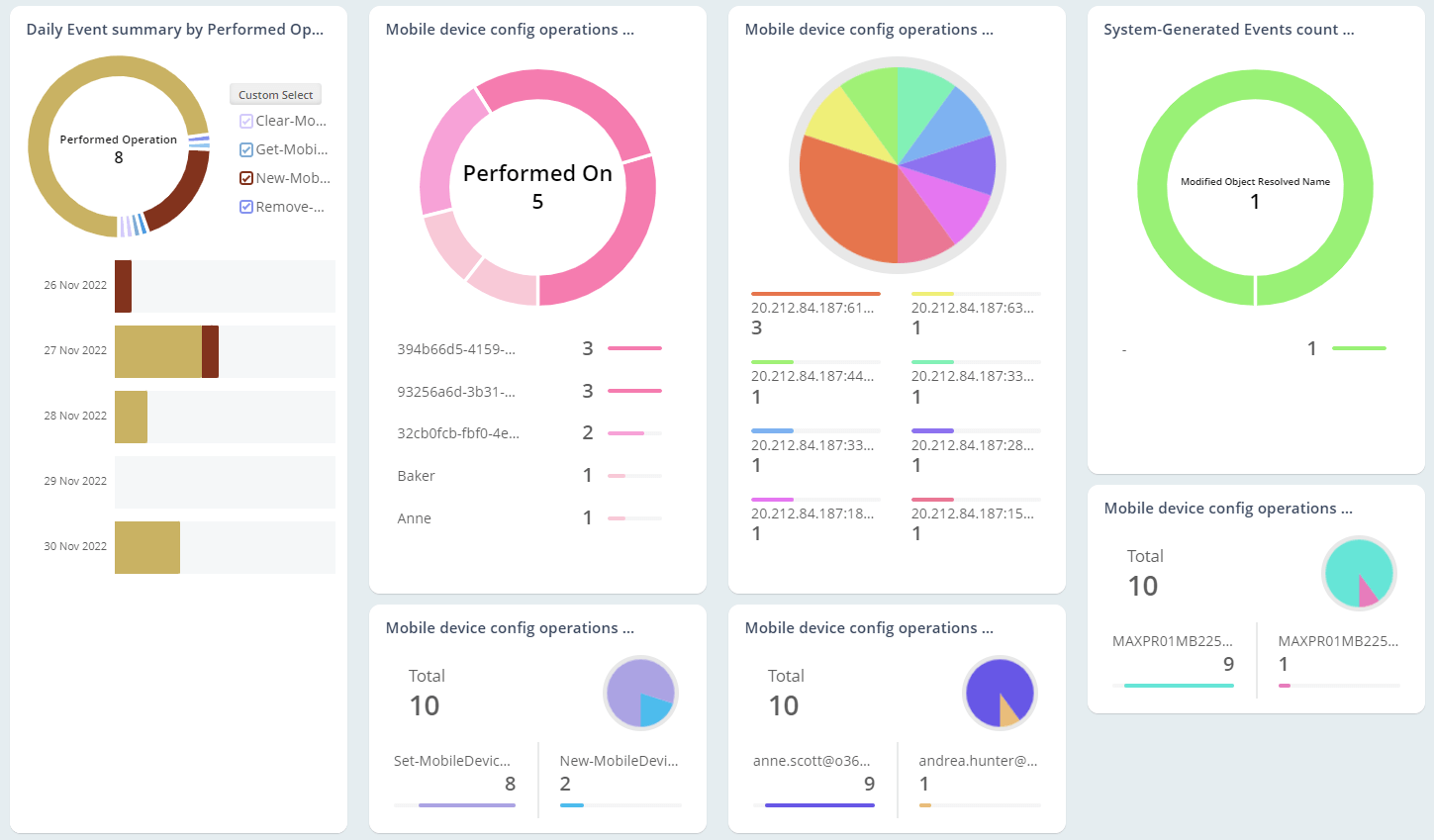
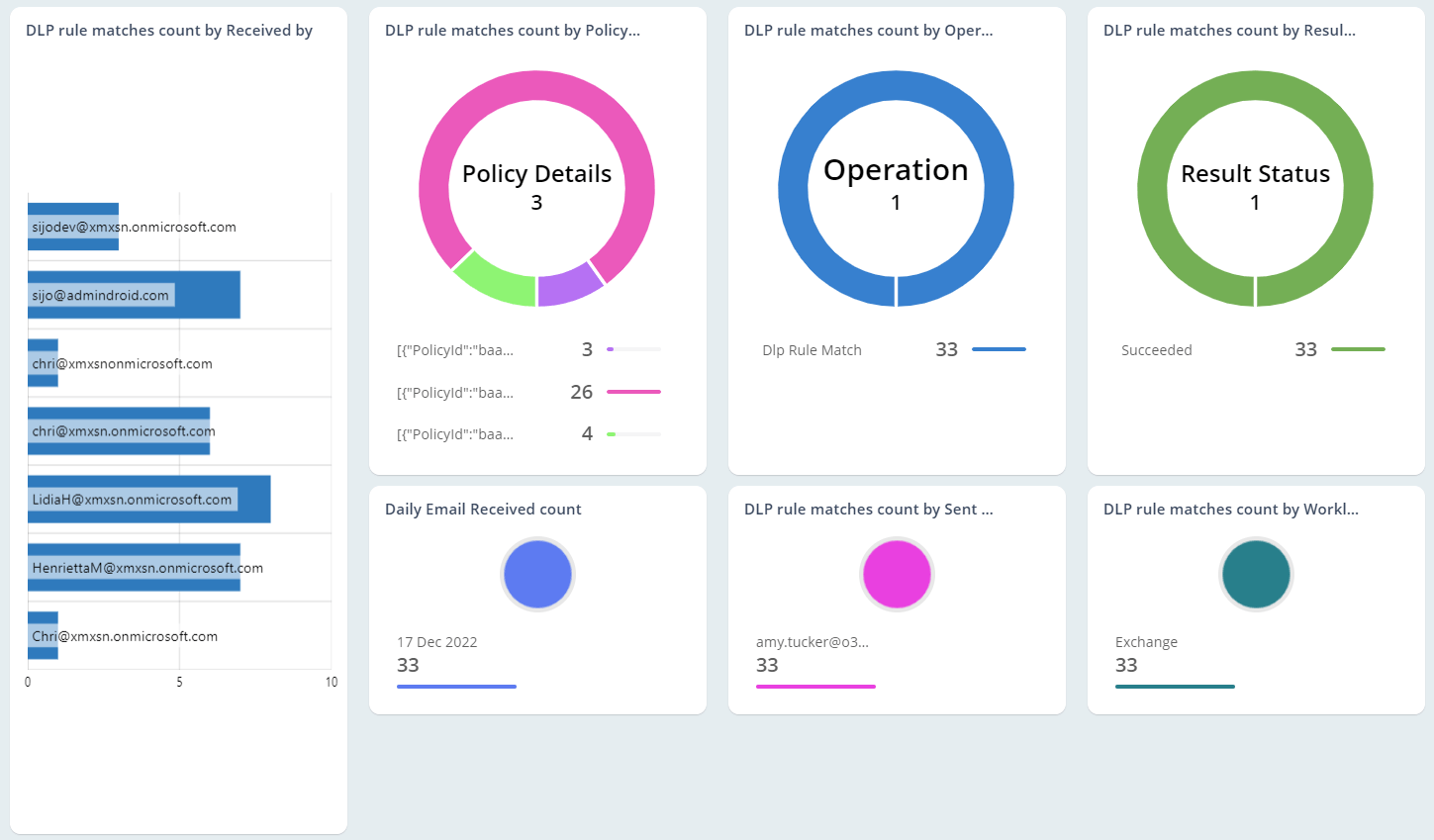
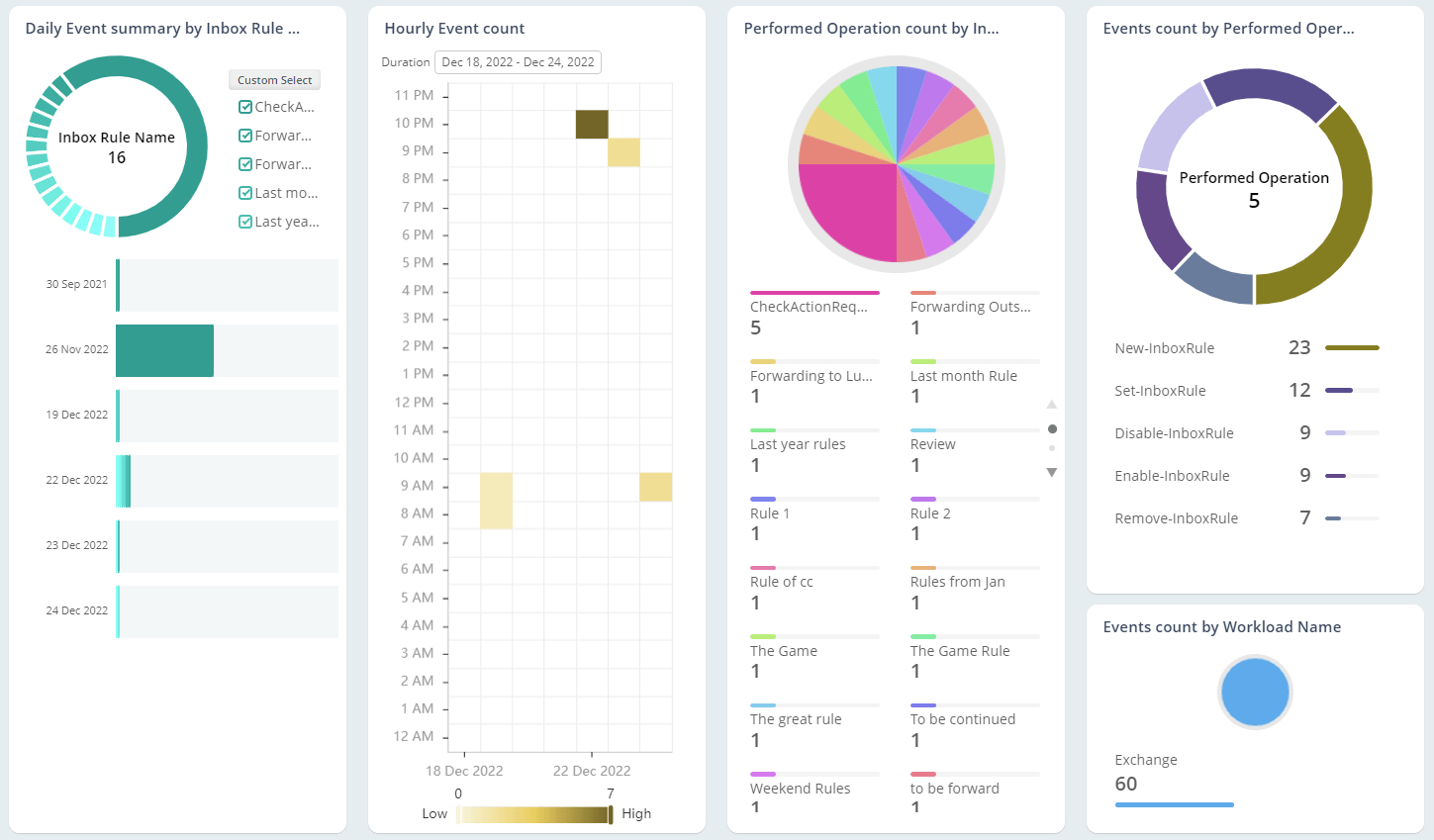
Exchange Online Auditing
As the mailbox is loaded with business-critical information, they are highly prone to email abuses. So, monitoring Office 365 mailbox activities, access permissions, and configuration changes are essential in the organization. Native mailbox auditing includes inherent challenges, like individual cmdlets for retrieving each activity and not being able to control plenty of noise in security audit logs. On the other hand, AdminDroid offers 65+ extensive auditing reports that are integrated with valuable insights for effective Exchange mailbox auditing.