What are the benefits of enabling MFA in Microsoft 365?
MFA (Multi-factor authentication) unlocks a realm of robust security, shielding user accounts with multiple layers of protection. Here are five key advantages of using multi-factor authentication in Microsoft 365:
- Increased Microsoft security: MFA requires users to provide two or more ways of authentication when they sign in. This helps to prevent unauthorized access, even if a user's Office 365 password is compromised.
- Reduced risk of data loss: MFA can help to reduce the risk of data loss by preventing malicious Microsoft 365 sign-ins to your organization.
- Improved compliance: Many Microsoft 365 organizations' regulations such as HIPAA, GDPR, CJIS, and more require admins to implement multi-factor authentication. By using MFA, you can help to ensure that your organization is compliant with these regulations.
- Protection against phishing attacks: Even if a user unknowingly discloses their password to a malicious website or email, the second authentication factor acts as a barrier.
- Credential theft mitigation: MFA safeguards against cybercriminals using automated tools to test numerous username-password combinations. The second authentication factor resists duplication, reinforcing the account effectively.
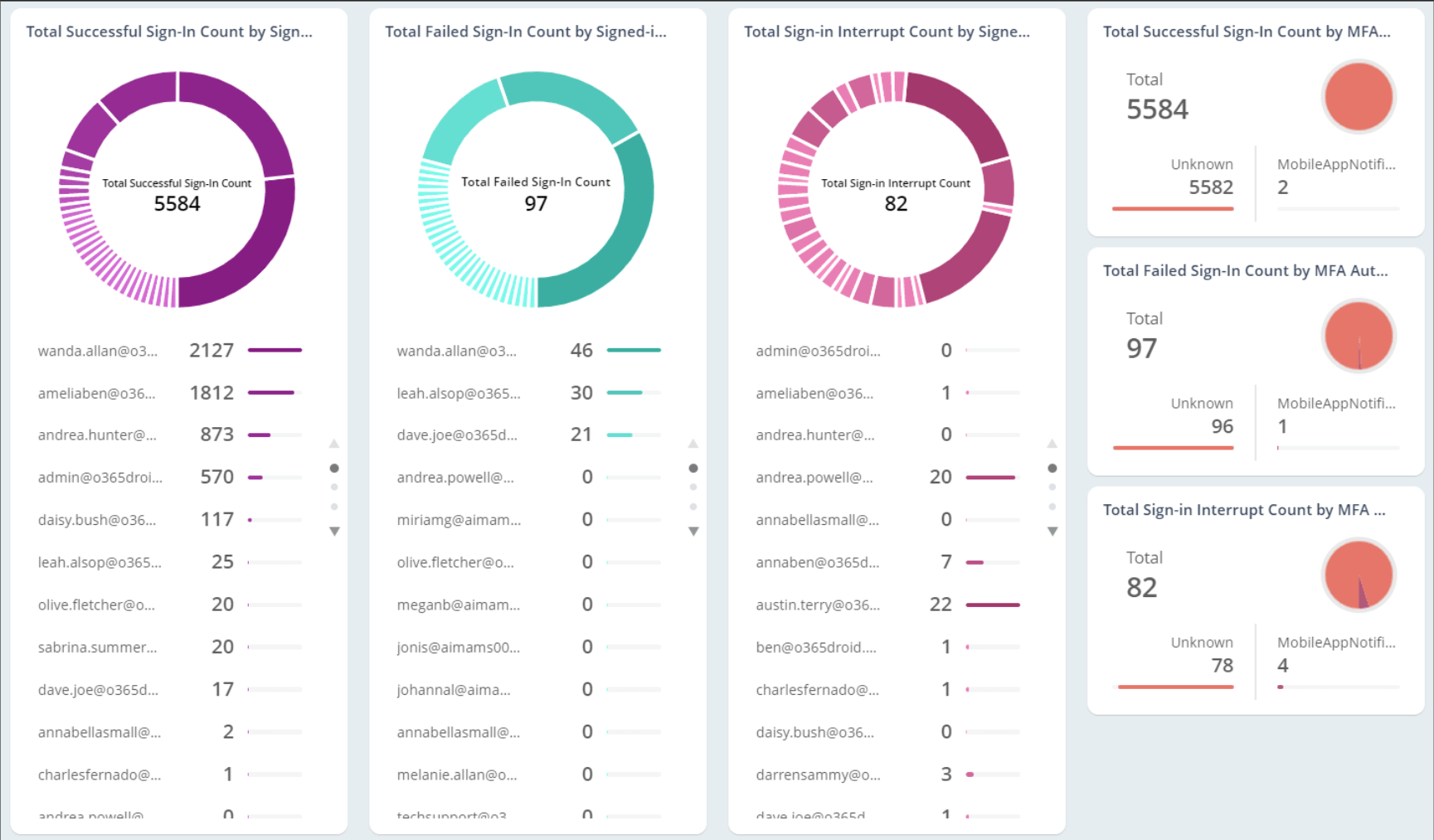
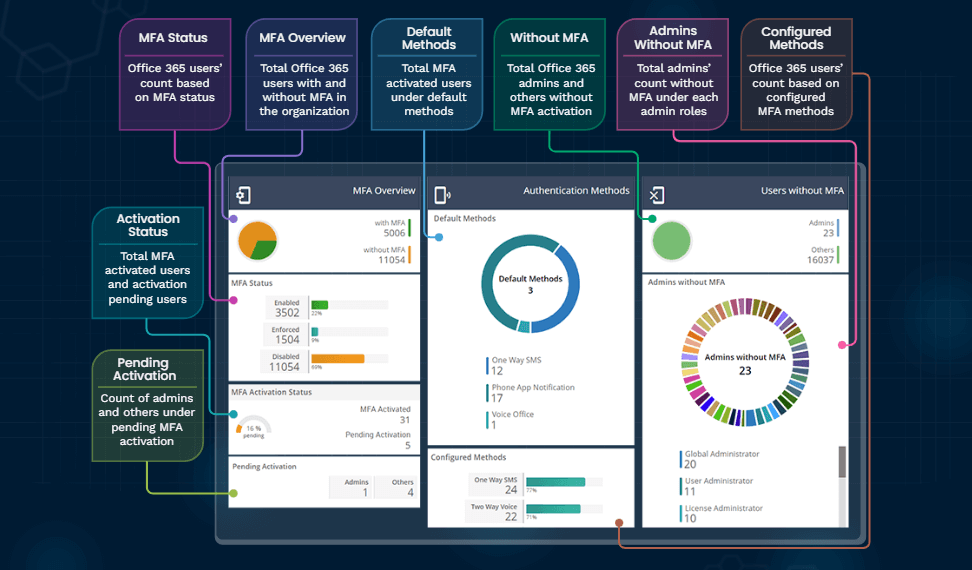
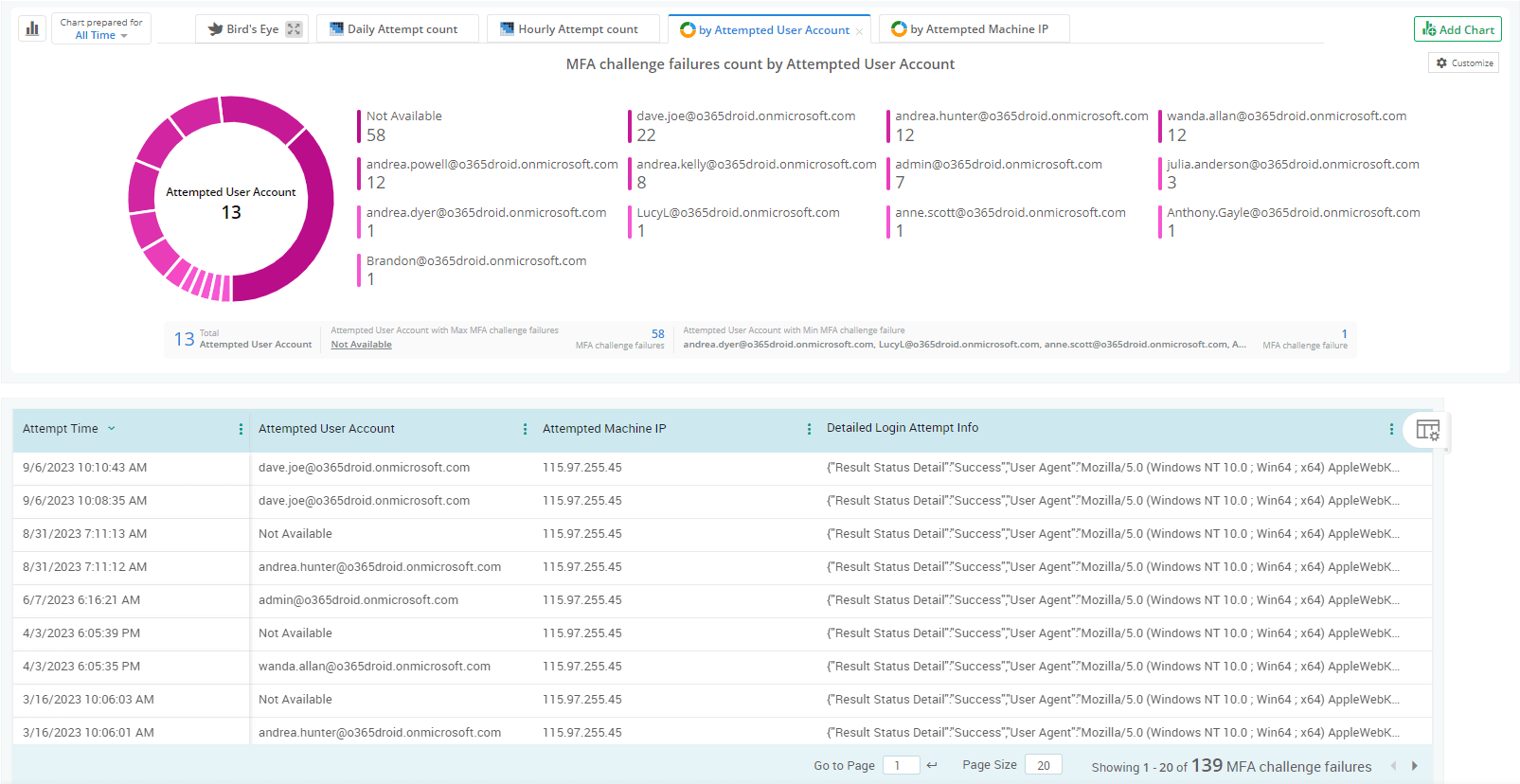
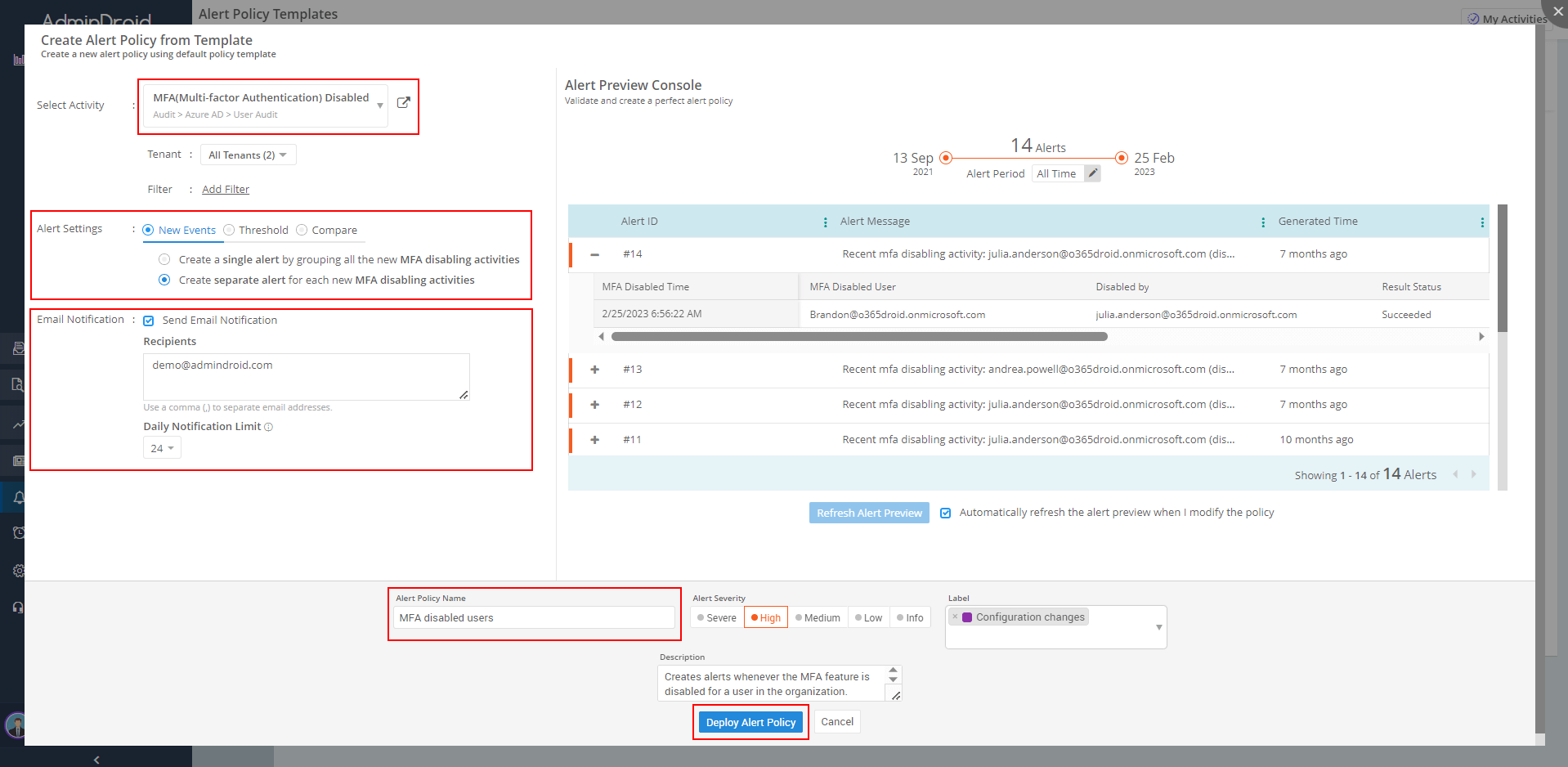
AdminDroid: Protect your organization with better MFA monitoring.
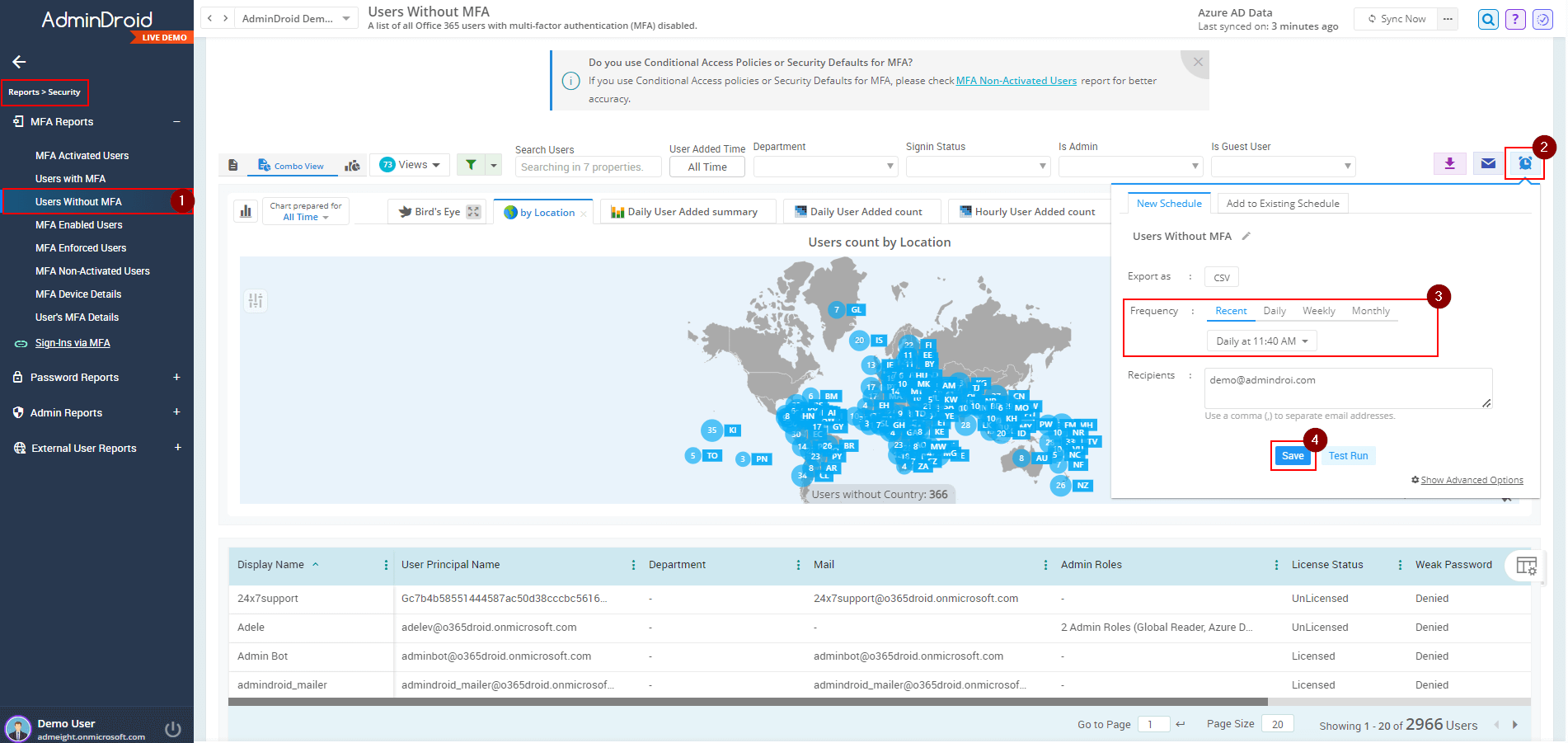
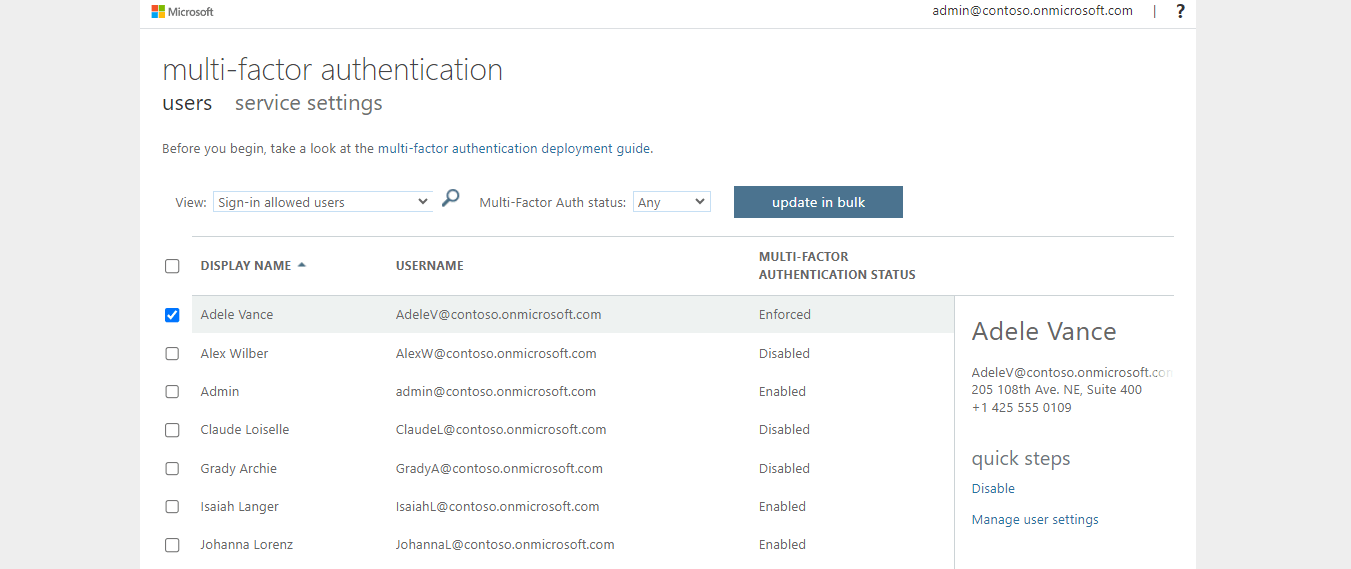
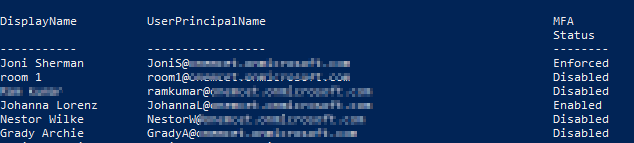
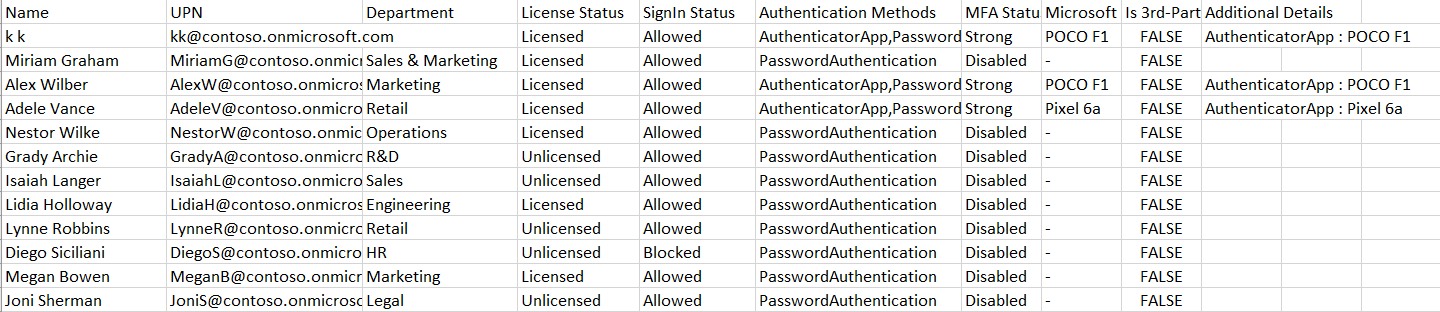
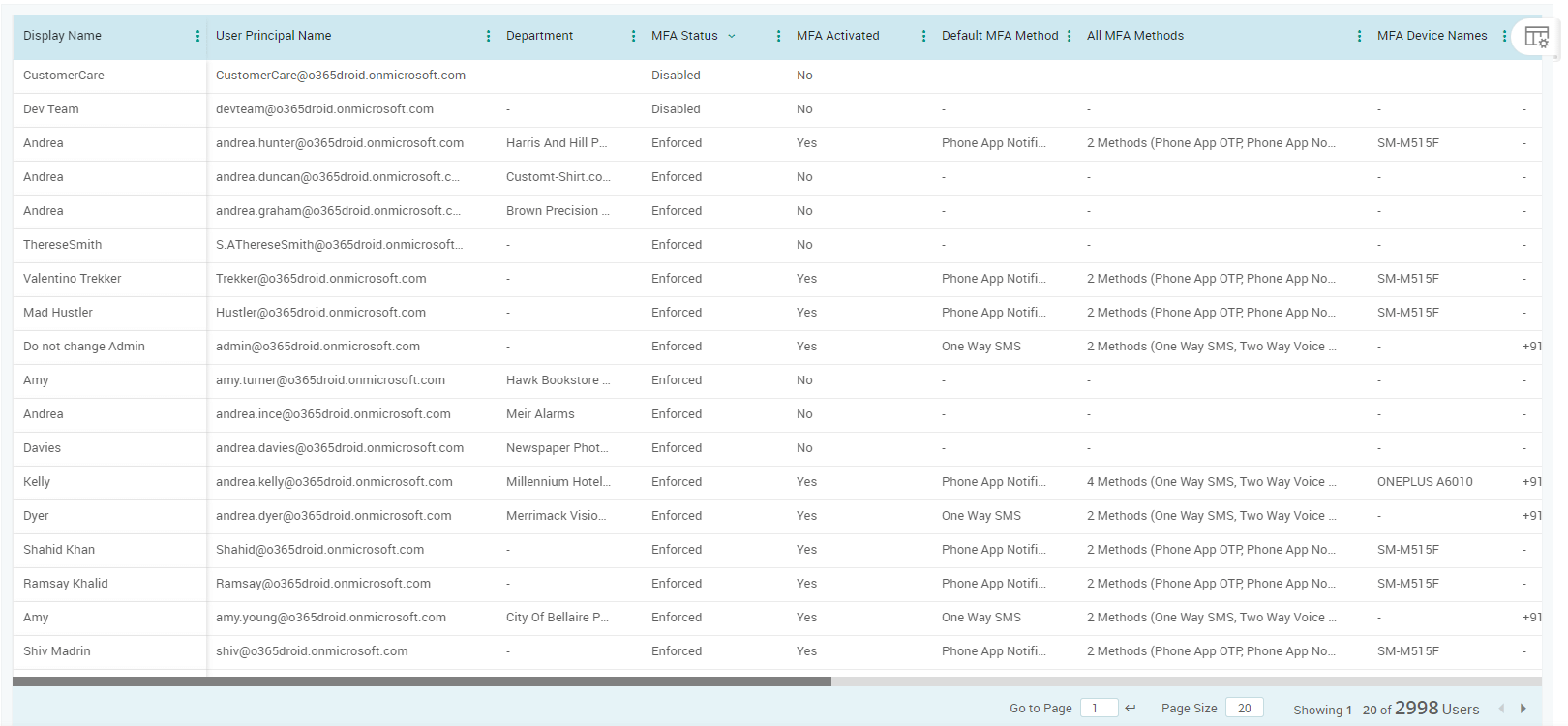
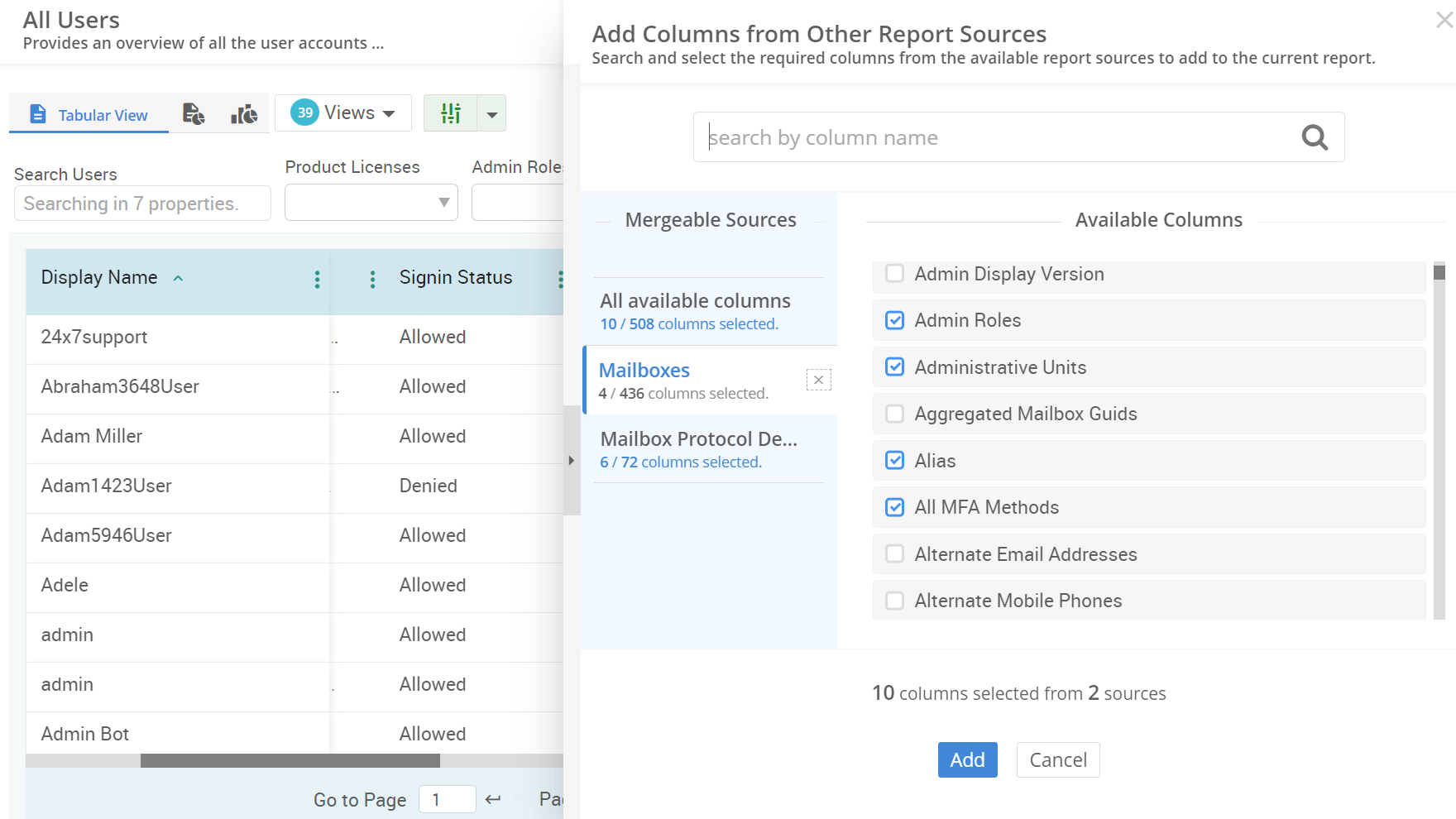
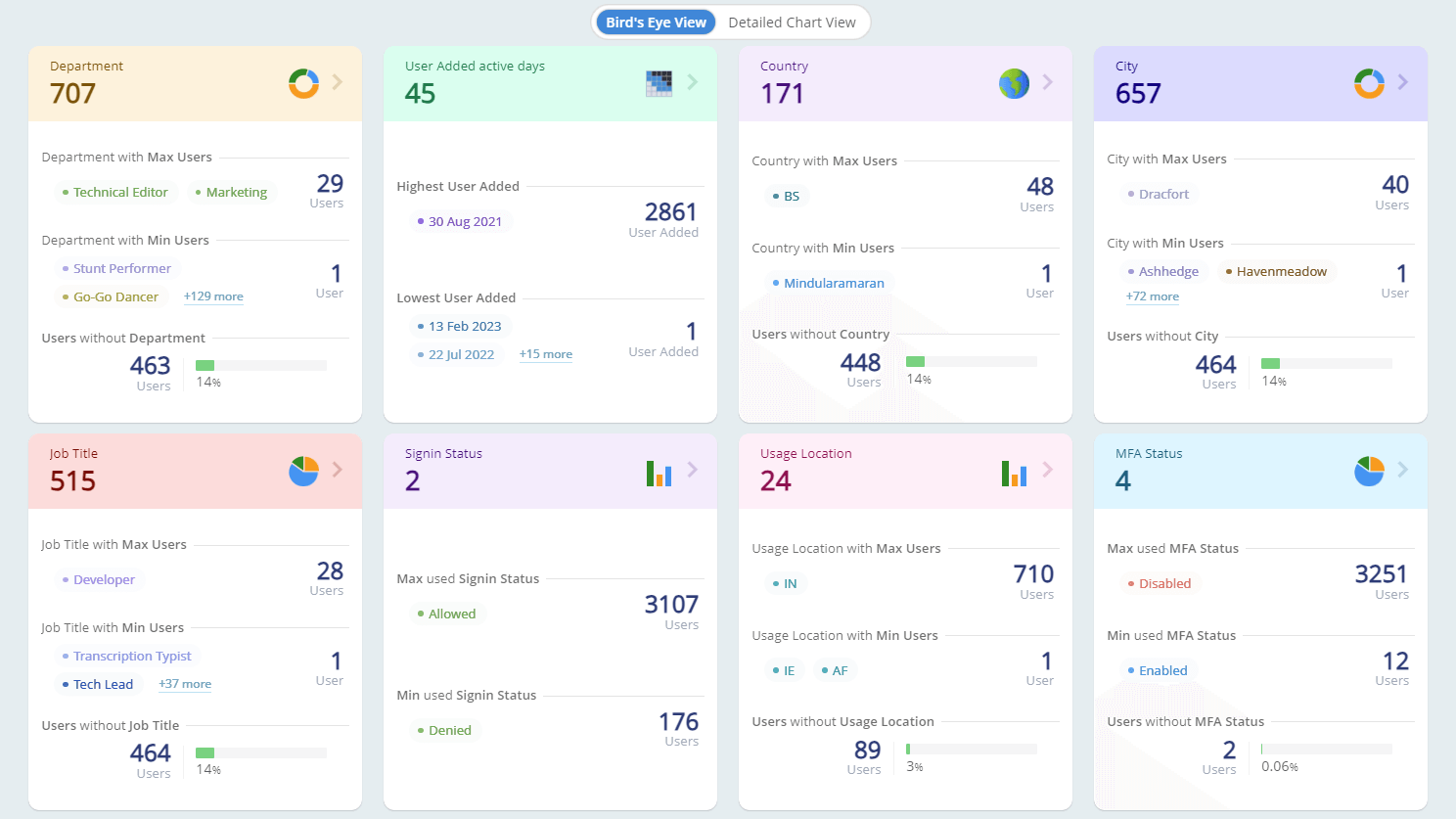
- Use the dedicated Users without MFA resided under to list the users with multi-factor authentication (MFA) disabled.
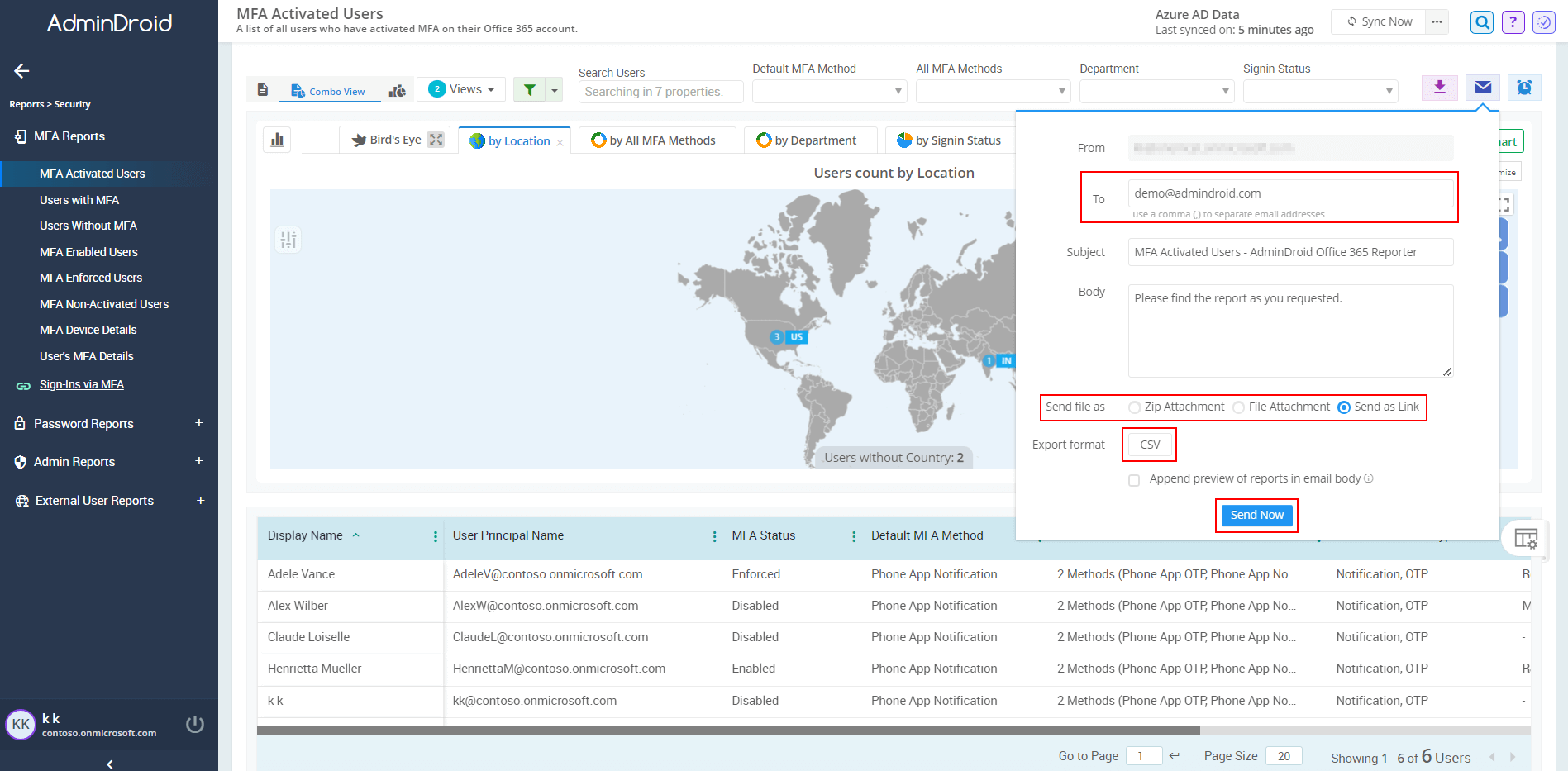
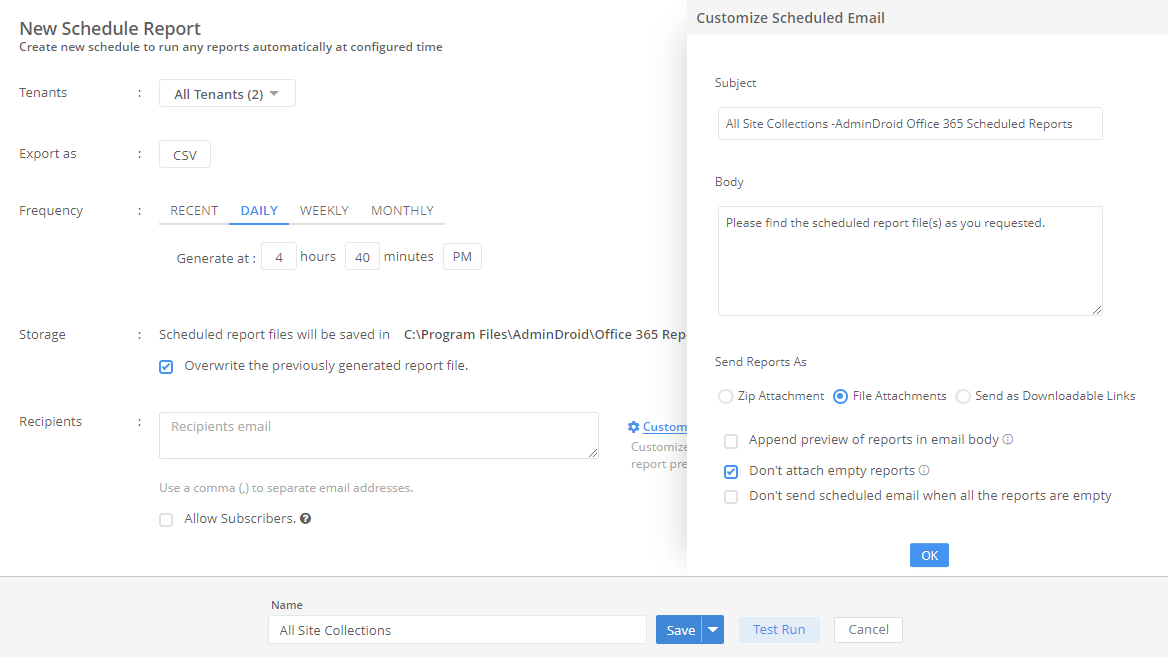
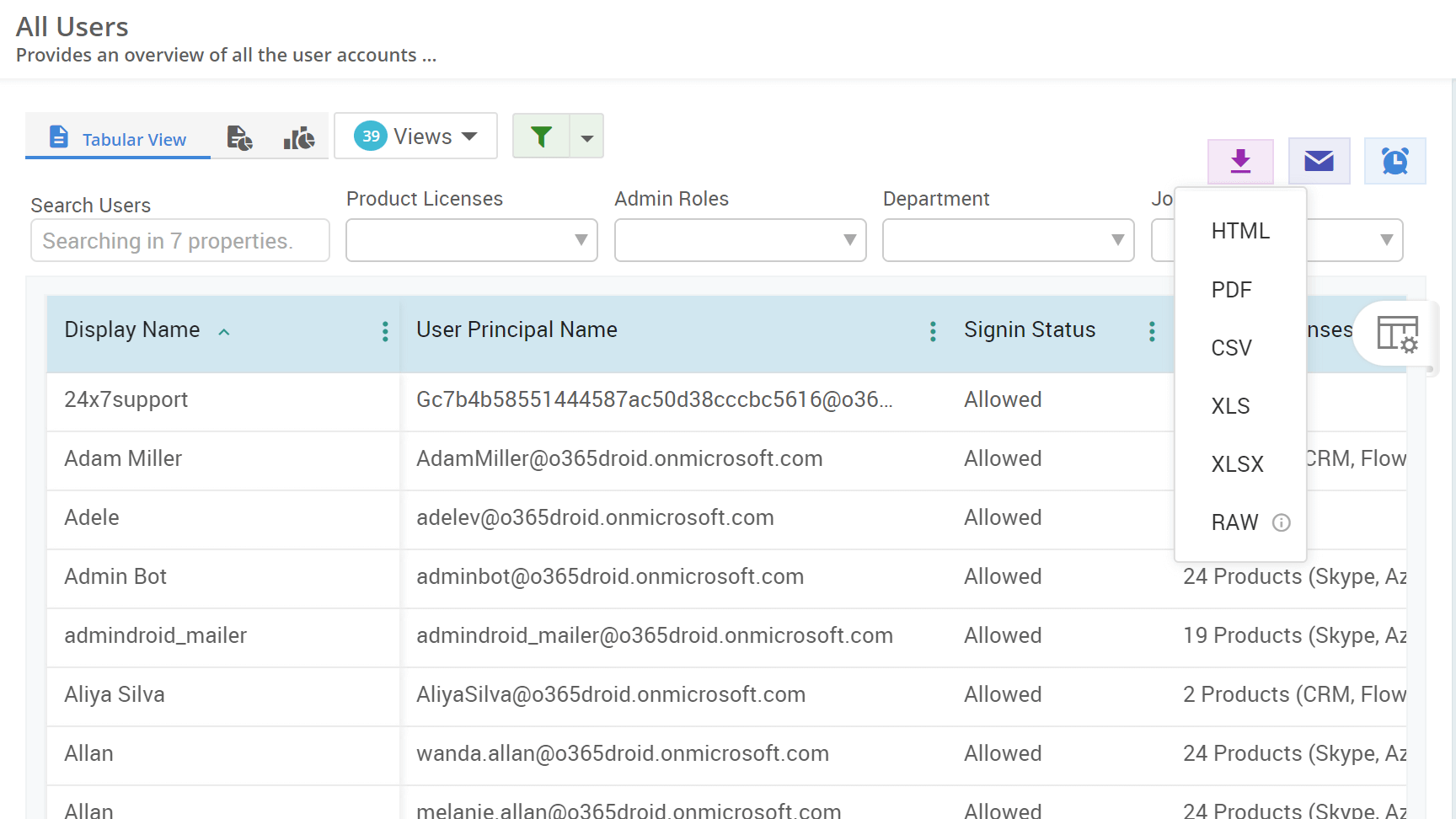
- We recommend utilizing the Quick Schedule⏰ feature which periodically sends the report to your inbox. Follow these steps to activate the quick scheduler option.
- Set frequency to be scheduled and save the scheduler with name.
- Now it is easy to frequently monitor on users whose MFA is disabled.