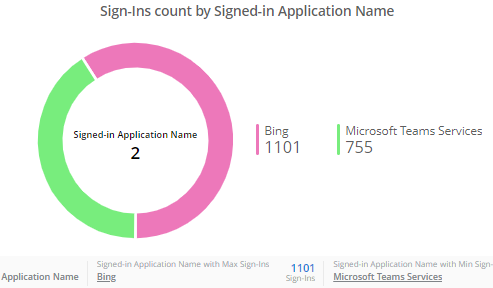
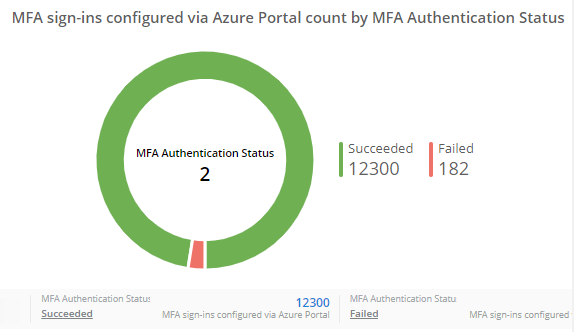
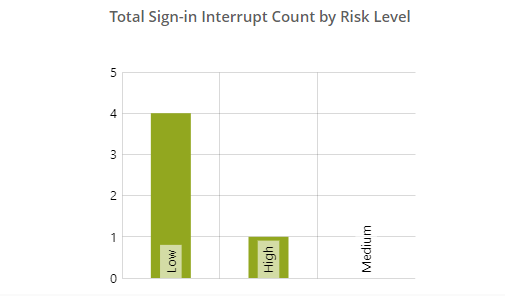
Microsoft 365 Sign-in Analytics and Alerting
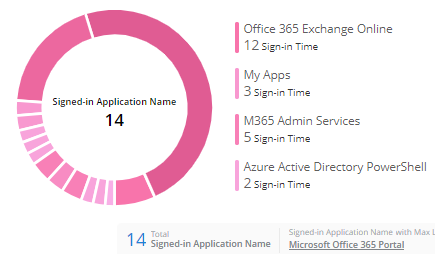
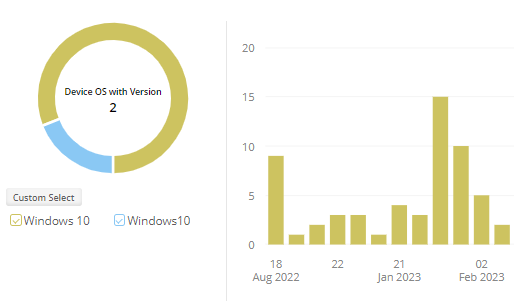
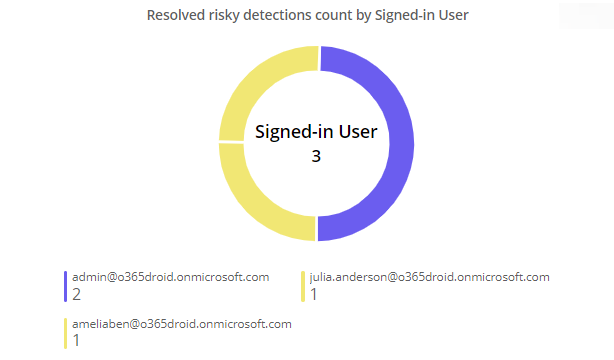
Do you want to ensure the safety of your Microsoft 365 sign-ins? AdminDroid is your ultimate solution, offering detailed insights into Microsoft risky sign-in analytics, user sign-in patterns, and more to help you proactively safeguard your sensitive data.